
NTT DATA supports Clients operating in different Sectors to address OT Cybersecurity
Companies across diverse market sectors - from Manufacturing to Energy & Utilities, from Chemicals to Infrastructure – are, also due to regulatory pressure, taking steps to strengthen Cybersecurity controls within their OT (Operational Technology) environments. This article outlines the context, details NTT DATA's proposed approach, and provides a few practical examples.
Industry 4.0 and the new importance of Cybersecurity in the OT Domain
The transition towards the "Industry 4.0" model - characterized by a massive digitalization of Operations, the convergence between Information Technology (IT) and Operational Technology (OT) and the adoption of new technologies - is bringing significant advantages in terms of operational efficiency and process optimization, but it has also exposed OT systems to new and sophisticated cyber threats.
The abandonment of the complete technical and organizational segregation model ("air-gap") between IT and OT has introduced new important challenges in terms of cybersecurity.
In such a context, where a need is perceived to extend the Cybersecurity domain from IT towards OT, NTT DATA supports its Customers in the transition and transformation of their OT environment, processes and infrastructures.
We are well aware of the specificities of OT environments and we know that taking care of their Cybersecurity requires a strategy capable of organically addressing a series of organizational and technical aspects.
NTT DATA's approach to OT Cybersecurity
Companies involved in this transformation process should follow a gradual and structured path that allows them to improve their security posture without impacting operations.
Well aware of the specificities of the Companies operating in the various market sectors interested in this transformation and of the fact that an OT Cybersecurity program must necessarily be tailored to the needs, priorities and spending capacity of each reality, at NTT DATA we have designed an incremental path to support our Customers who intend to extend Cybersecurity control to their OT area.
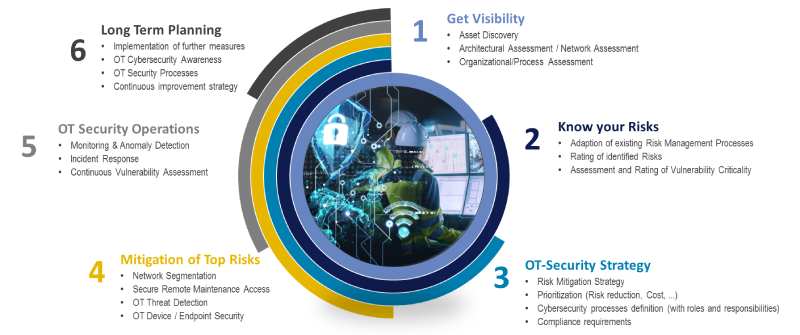
Figure 1: The structured and progressive approach proposed by NTT DATA for OT Security
This path consists of several phases, described below.
- Acquisition of awareness of company OT assets, infrastructure and internal security processes.
It is essential for companies to have full visibility of what their OT assets are and how they are interconnected with each other and with the rest of the IT infrastructure; this can be achieved through asset discovery activities for the creation and dynamic updating of a detailed asset inventory (possibly coordinated with the company CMDB).
From a technical point of view, it is also important to carry out an assessment on architectural and network aspects.
On top of that, an organizational assessment is useful to verify the correct attribution of roles and responsibilities in the cybersecurity field (RACI matrix), as well as the presence of adequate security processes, procedures and policies. - Cyber risk assessment.
An in-depth cyber risk assessment (in an objective and context-aware fashion) is essential to identify potential threats that could compromise the security of OT systems. This process should include analyzing vulnerabilities, evaluating the potential impact of attacks, and determining appropriate mitigation measures. - Definition of an OT Security strategic plan.
Based on the results of the risk assessment, companies should develop a comprehensive strategic plan to improve the security of their OT systems. Interventions should be prioritized with a risk-based approach, which also takes into account compliance with regulations (NIS/NIS2 Directive, National Cyber Security Perimeter, New Machinery Regulation, etc.) and industry standards (ISA/IEC 62443, NIST SP 800-82, etc.) and of course also considering the associated costs. This plan should include clear objectives, specific actions and guidelines for managing risks and protecting systems. - Mitigation of key risks.
Once the strategic plan is defined, companies should focus on implementing measures to mitigate the identified risks.
A solid starting point is to use the Purdue Model as a reference, always useful for clearly defining security levels and outlining risk mitigation strategies for the different levels of control and management of information and processes.
Technical countermeasures might include the implementation of network segmentation (with the creation, first and foremost, of an industrial DMZ at the border between IT and OT networks), the application of improved access controls (for example using Multi-Factor Authentication for remote access), updating security policies and implementing advanced incident detection and response technologies. - OT Security Operations.
It is important that companies implement processes and procedures for continuous monitoring of the security of OT systems, as well as for the effective management of security incidents. This might include the implementation of passive network traffic monitoring systems (Intrusion Detection Systems), the analysis of anomalous behavior and the implementation of incident response workflows, under the aegis of a Security Operations Center (SOC) with qualified staff with OT Security know-how. - Long-term planning for "continuous improvement".
Finally, companies should develop a long-term strategy for continuously improving the security of their OT systems. This may include periodically reviewing security policies and procedures, setting cybersecurity training and awareness programs, and implementing innovative technologies and solutions to address new emerging threats.
Using the Claroty xDome Platform to support the implementation of our approach
Our structured approach may be supported, for a number of aspects, with the adoption of an OT Threat Detection & Prevention Platform, such as Claroty xDome.
xDome is a modular, SaaS-powered, OT-specific platform, which empowers industrial organizations with complete asset visibility, helps identifying vulnerabilities and evaluating risk, optimizes threat detection, and enables the deployment of Zero-Trust protective controls through a wide ecosystem of integrations.
xDome, with its comprehensive set of features, is an enabler for:
- clear visibility of OT assets and network (which allows for proper management),
- informed (risk-driven) cybersecurity decision making (which empowers wise governance),
- accurate real-time anomaly detection (that triggers immediate incident response).
Asset Discovery
Having an accurate and detailed asset inventory is the foundation of any cybersecurity initiative to mitigate the risk and reduce the "attack surface" of the OT environment.
Claroty supports asset discovery with passive and/or active methods that are particularly effective thanks to a wide coverage of a wide range of OT-specific network protocols.
Once assets have been discovered (with a rich set of attributes), they are classified and presented in an effective and flexible console.
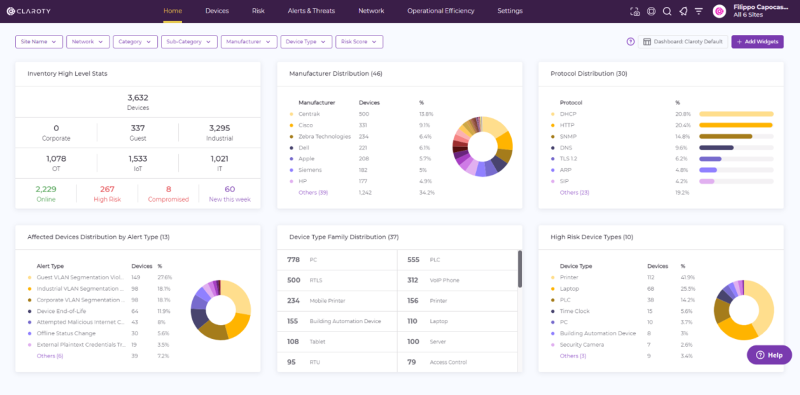
Figure 2: Claroty xDome (default) Home Dashboard
Vulnerability and Risk Management
xDome automatically correlates every asset with an always up-to-date set of known vulnerabilities coming from a huge database of CVEs and other weaknesses.
With a domain-specific perspective, xDome provides context-aware risk evaluation.
Among the features provided by Claroty xDome for Risk Management, there is a powerful tool to simulate the application of security countermeasures and to evaluate the potential benefits in terms of risk mitigation. Moreover, it automatically provides specific recommendations to reduce risk and improve the overall cybersecurity posture.
Network Protection
Being an Intrusion Detection solution, xDome does not directly enforce network rules, but it provides very useful features to support the implementation of Network Segmentation.
Backed by deep domain expertise, xDome leverages the visibility it provides into OT/IoT assets and their behavioral patterns to automatically recommend, define and monitor network communication policies.
Integration with other security solutions, such as Firewalls, NACs and SOARs, allow for tailored enforcement of network segmentation policies.
Moreover, Claroty offers a solution for Secure Remote Access, designed on-purpose for the industrial domain.
Threat Detection
Claroty xDome continuously monitors the OT environment and uses both Deep Packet Inspection and AI-based Anomaly Detection to support real-time Threat Detection.
The solution automatically profiles all the assets and their communication patterns in order to generate a baseline for normal network behavior, characterize legitimate traffic to weed out false positive anomalies, and alert users in real-time to both known, unknown, and emerging threats.
Using the Claroty xDome to provide OT-SOC Managed Services
Enterprises are increasingly integrating OT security with their IT Security Operations Centers (SOCs), which - if executed properly - can deliver significant performance and efficiency advantages.
However, a SOC may be overwhelmed with an abundance of alerts, many of which may be false positives.
Claroty leverages proprietary algorithms - based on the unique context and specific circumstances in which each alert is triggered - that limit the occurrence of false positives.
The Claroty Platform delivers contextual insight into OT environments that streamlines and accelerates alert policies, assessments, triage, and other components of the alert management lifecycle.
Claroty can group interrelated events into a single alert: the result is a consolidated, contextualized view of the full chain of events that enables Root Cause Analysis, thereby making it significantly easier to investigate, determine what has happened end properly trigger an incident response process.
The following figure shows an example of how you can analyze and contextualize an alert with Claroty.
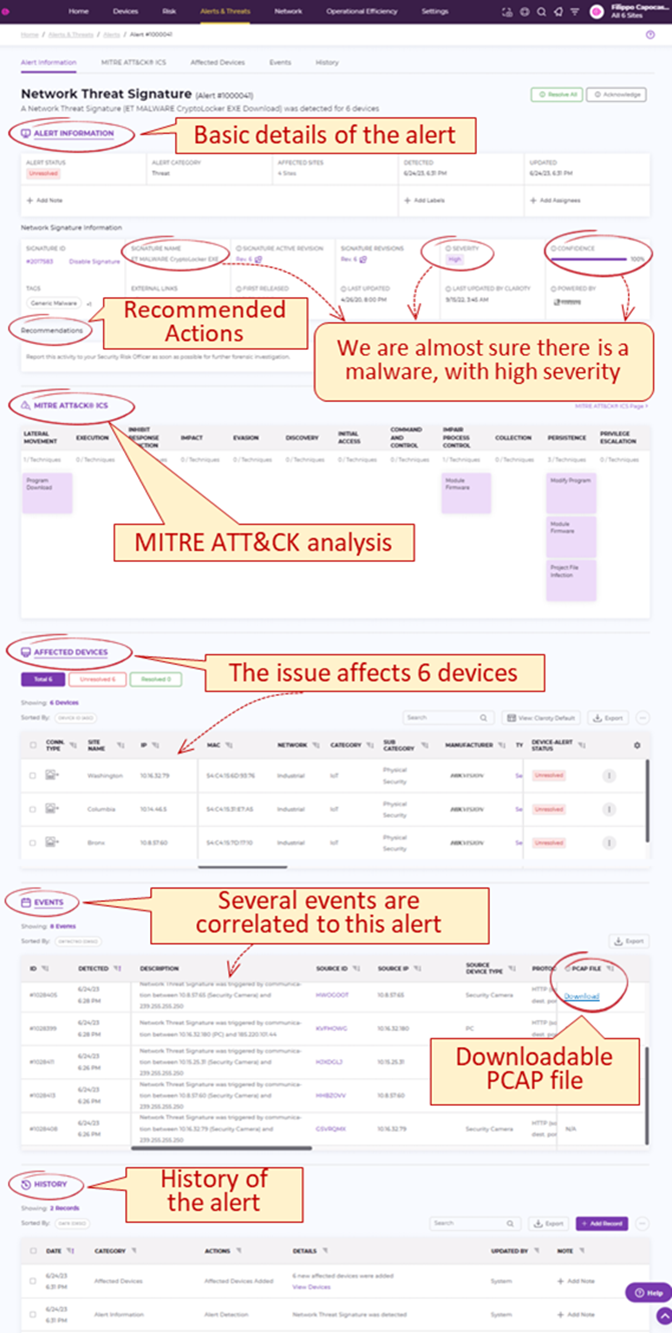
Figure 3: Example: contextualization and analysis of an alert
Practical experiences in projects with Claroty xDome
NTT DATA has implemented the Claroty xDome Platform for several Clients; for example, we may present a couple of "success stories" in Italy and Austria.
- Implementation for the Company operating an Italian Motorway
NTT DATA has supported the Company operating the Motorway in a Region of Italy to set-up and fine-tune an OT Threat Detection & Prevention platform overlooking a distributed OT Infrastructure, consisting of a significant number of devices (several types of sensors, dynamic road signs, tolling systems, CCTV, emergency systems, intercom, etc.).
The Client wanted to gain visibility on its OT Network, enable a process of Vulnerability and Risk Management and extend the control of the existing IT SOC to the OT environment.
NTT DATA proposed and executed a PoC with Claroty xDome: already after a couple of hours from the deployment some vulnerabilities were notified and promptly fixed by the SOC and the OT personnel; a complete and detailed report has been provided to the Client at the end of the PoC.
The solution proposed by NTT DATA has been chosen by the Client in a range of 4 different products they have extensively tested in their environment: a key success factor was the accuracy of the report created as an outcome of the analysis of the OT environment executed with xDome. - Implementation for an Austrian Company in the Steel Industry
The Customer operates multiple sites globally to produce steel and special steel products.
Steel production is a highly automated process. In case of a cybersecurity incident, it is not possible to stop operation of steel production. A single cyberattack may destroy a complete production site. This risk, as well as regulatory compliance requirements, was the main starting point of a security initiative of the Customer.
As in many OT environments, a detailed knowledge about assets, vulnerabilities and resulting risks was not available.
After a detailed evaluation of multiple solutions, the Customer decided to engage NTT DATA to implement and rollout Claroty xDome in their sites. One of the main reasons for choosing Claroty xDome was the easy way of implementation and rollout. After a couple of days, a complete inventory of the overall OT environment in one site was available, and communication anomalies and threats were detected.
The xDome dashboard provided to the Client a risk-based view of assets and allows effective prioritization of remediation actions to address risk exposures.
As testified by these "success stories", NTT DATA has practically demonstrated that our well-structured approach to OT Cybersecurity, supported by the adoption of an effective domain-specific platform such as the one provided by Claroty, may be adopted by Clients operating in very different Market Sectors to significantly improve their Security Posture in the era of the IT/OT convergence.
Partnership between NTT DATA and Claroty
NTT DATA and Claroty have an active collaboration on the Market, both taking advantage of the synergy between the know-how of the professional services provided by the System Integrator and the advanced technology solution provided by the Vendor.
NTT DATA is proud to be the 2024 Global Partner of the Year for Claroty:

Figure 4: 2024 Claroty's Global Partner of the Year: NTT DATA

Graduated with honors in Computer Engineering at the University of Calabria (UniCal), Filippo Capocasale has spent his whole career, spanning over more than 20 years, in the Cybersecurity sector.
He managed projects of Architectural Design, Implementation and System Integration for major Clients in Italy and other Countries. He spent over a year in Tokyo, working in Automotive Cybersecurity R&D. Currently he leads the «Cyber-Physical Security & Innovation» Practice in the Security Service Line of NTT DATA Italia: his responsibility encompasses OT/IoT/IIoT Security, Automotive Cybersecurity and Innovation in the Cybersecurity domain.

Christian Koch is Senior Vice President of Cybersecurity for IoT/OT, Innovations, and Business Development at NTT DATA. He leads initiatives focused on cybersecurity innovations, including AI security, Zero Trust and OT security, and actively participates in global working groups for security innovations within the NTT Group. Since joining NTT Group in 2017, he has held various roles, concentrating on cutting-edge cybersecurity technologies and consulting strategies across multiple industries. Christian is a graduate engineer in information technology and has more than 25 years of experience in the cybersecurity field.
Related links
