
The Role of Automation in Cybersecurity Operations
In response to increasingly complex cyber-attacks, security operations such as monitoring system logs and incident response are becoming more important. However, there is a shortage of specialists across the security market. In this paper, we propose a better practice for improving the efficiency of security operations based on the know-how for evolving security operations using NTT Data’s UnifiedMDR services.
Recent Trends in Cybersecurity Specialist Supply and Demand
With the recent intensification and increasing complexity of cyber-attacks, security operations are becoming more important. Security operation and response teams such as SOC (* 1) and CSIRT (* 2) are constantly required to execute many operational tasks.
However, as the adoption of zero-trust architecture has progressed in the world, the number of professionals dedicated to protecting the security of diversified IT environments has not been sufficient worldwide. According to an international investigation group, research shows that there is a shortage of about 3.9 million cybersecurity professionals worldwide. (Figure 1)

Figure 1: Number of data breaches and security professional gap
Security operations, such as analysis of computer and network logs and incident response, require a high level of expertise and skills developed through multi-year experience. Keeping staff to handle these tasks, reducing operational costs, and establishing a stable operating system are important challenges for organizations responsible for cybersecurity.
- (* 1) Security Operation Center (SOC): A team that continuously monitors computer and network logs to analyze, detect and respond to cyber-attacks.
- (* 2) Computer Security Incident Response Team (CSIRT): A team that analyzes, investigates, and responds to security incidents.
- (* 3) We created the graph based on data from Statista, ”Annual number of data compromises and individuals impacted in the United States from 2005 to 2023 ”.
- (* 4) Based on research by ISC2, "Cyber Workforce Study 2020 -2023," we created a graph. Please refer to the "Workforce Gap & Estimate" section of each report for detailed figures.
Challenges in Cybersecurity Operations
According to the "Textbook for SOC and CSIRT” (* 5), which serves as a framework for the services that a security-responsible organization should provide, 64 services in 9 categories are defined as those that should be implemented in the cycle from planning and construction to operation. Of course, few teams can complete and implement all these functions in one organization, so it’s important to design an operation that combines in-house resources with outsourcing.

Figure 2: Security teams have a variety of tasks
As shown in Figure 2, there is a wide variety of tasks that a security-responsible organization should perform. In particular, it should not take too much time to analyze and respond to false positives or unimportant security alerts in log analysis, causing the SOC analyst to overlook truly important breach. CSIRT must also avoid a situation where the team is unable to devote resources to respond to an incident after it has occurred.
To solve these issues, we believe it is desirable to automate simple routine tasks that occur daily in an organization in-source. By doing this, the availability of operations personnel will increase and resources can be allocated to tasks that truly need to be focused.
-
(* 5)
ISOG-J (Information Security Operation providers Group Japan), “Textbook for SOC and CSIRT ”.
This standard document, developed by group of Japanese security operations companies, has been adopted by the ITU-U X.1060 (Framework for the creation and operation of a cyber defence centre) and it has been an international standard.
Evolving with NTT Data UMDR Service
Here are examples of NTT Data's efforts to improve security operations in response to the issues mentioned above.
NTT Data is developing Unified Managed Detection and Response (UMDR service), a next-generation managed security service for rapidly detecting and responding to security threats in the customer environment (* 6). NTT Data will make the most of the know-how we have accumulated over more than 20 years of experience in security operations and incident response to address customer security governance globally.
For the UMDR service, we have built security service infrastructure called "SOC Solutions" to enhance security operations, as shown in Figure 3. Each service in the diagram consists of a combination of open-source tools and enterprise security service to provide functions to the operations team.
We have been able to reduce the cost of security operation specialists by utilizing SOC solutions to automate key tasks such as initial analysis of operational alerts, in-depth investigation based on threat information, and ticketing and management to communicate with customers.

Figure 3: UMDR service infrastructure evolved by SOC solutions
Benefits of Improving Operation Infrastructure
Let us go through the specific features and benefits that SOC solutions provide as a security service infrastructure.
Automation: Automatic Response to Security Events
Automation is a service that provides automation of operations using solutions commonly classified as SOAR (* 7). In accordance with the playbook (* 9) predefined in no-code development (* 8), Automation works with other services to investigate and analyze detected events in SIEM and EDR, isolate endpoints, and perform other necessary processing. It plays a central role in the operational sophistication provided by SOC solutions.
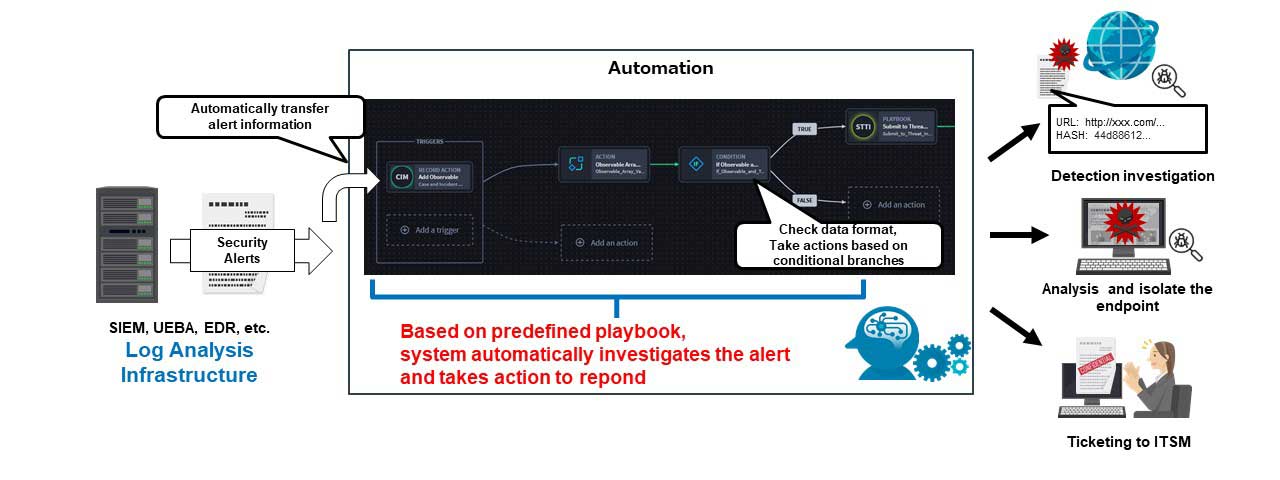
Figure 4: Automation and reducing work time through SOAR
- (* 7) SOAR (Security Orchestration, Automation and Response): Technology and solutions for rationalizing and automating security operations
- (* 8) No code development: A method for developing applications and systems without writing a source code
- (* 9) Playbook: Settings that define action groups such as investigations and response and their execution flows
Ticketing/Portal System: Customer Communication
Ticketing/Portal System utilizes ITSM solution (* 10). Automation creates a ticket and manages individual cases that describe the handling status of incidents, which will speed up communication between security response organizations and employees and customers. It also functions as a portal site for service catalogs and customer inquiries.
- (* 10) ITSM (IT Service Management): System that enables service providers to efficiently and effectively manage the IT services they provide, and a solution that provides these functions.
Threat Intelligence: Cyber Threat Information Management
Threat Intelligence provides an IoC (* 11) for making decisions if malicious or not on security events. Referencing this threat information, Automation services can instantly decide whether a security event is truly an incident that must be responded to. The UMDR service utilizes NTT Data's multi-million record threat information database as IoCs.
- (* 11) IoC (Indicator of Compromise): Information recorded in the system log in the event of a cyber-attack. Specifically, it is threat information such as the domain name, IP address, and file hash value used in the attack.
Operational automation and ITSM solutions provide the following benefits by increasing the sophistication of the security service infrastructure:
-
- Benefits to employees and customers who receive security monitoring services
- - Rapid and flexible cooperation with security response organizations through ITSM
- - Prevention of the spread of malware infection through automatic endpoint isolation and control of network equipment
-
- Benefits for security-support organizations
- - Reduction of operational mistake caused by manual operations
- - Acceleration and timesaving of investigation and analysis tasks through work automation
- - Reduction of operator training costs by developing and reusing playbooks
Conclusion
It is important to prepare the process for security operations in advance. On the other hand, there is less focus on features that can enhance security operations. In this article, presented an example of how the introduction of automation and other security service infrastructure that support security operations can bring benefits to both employees, customers, and security-responsible organizations.
We provide global security monitoring and incident response capabilities through the UMDR service, which utilizes the SOC solution introduced in this article. If you are interested in improving your security operations, please feel free to contact us.
Yuki Oigo
NTT DATA Group Corporation
He was engaged in security operations, digital forensics, and incident response at NTTDATA-CERT. In 2019, he was moved to the Tokyo Olympic Organizing Committee, contributing to the improvement of cybersecurity. After returning to NTT Data, he has been working on the investigation of emerging technologies and global security service development. GIAC GCIH.
