Zero Trust
NTT DATA provides end-to-end services of Zero Trust, including policy formulation, implementation, and security operation and improvement, based on our rich global implementation experience.

Start Your Zero Trust Journey with NTT DATA
NTT DATA has the deep industry expertise and market-leading technologies to help you build and realize your vision of cybersecurity with Zero Trust. Partner with NTT DATA to benefit from agnostic and unbiased recommendations on your Zero Trust journey.
We will help you explore key considerations that need to be addressed and itemize initiatives based on criticality. Our holistic view of what others are facing across industries and against countless use cases helps ensure that your plans are future-ready.
NTT DATA Making Zero Trust Real
Leading experts on cybersecurity and information security at NTT DATA, Hiroshi Honjo and Steve Williams, share their learnings from NTT DATA’s implementation of Zero Trust and why Chief Information Security Officers (CISOs) must look to Zero Trust as the means to not only secure their business but also to continue earning the trust of their clients and customers.
Watch the video to learn how your organization can gain the benefits through implementing a Zero Trust framework.
Benefits of Zero Trust Model
Implementing Zero Trust requires a cultural change but brings many benefits including:
- Optimized vendor relationships and reduced training and license costs by leveraging a common set of technology
- Decreased security vulnerabilities by leveraging a common global security framework
- Cost reduction and optimization through standardization
- Cost and risk reduction through automation
- Decreased support costs and help-desk tickets
NTT DATA Making Zero Trust Real (10:40)
Meet Our Experts

Steve Williams
Enterprize Chief Information Security Officer, NTT DATA Services

Hiroshi Honjo
Head of Digital Growth, NTT DATA's Global Innovation Headquarters in Tokyo
NTT DATA’s Zero Trust Architecture
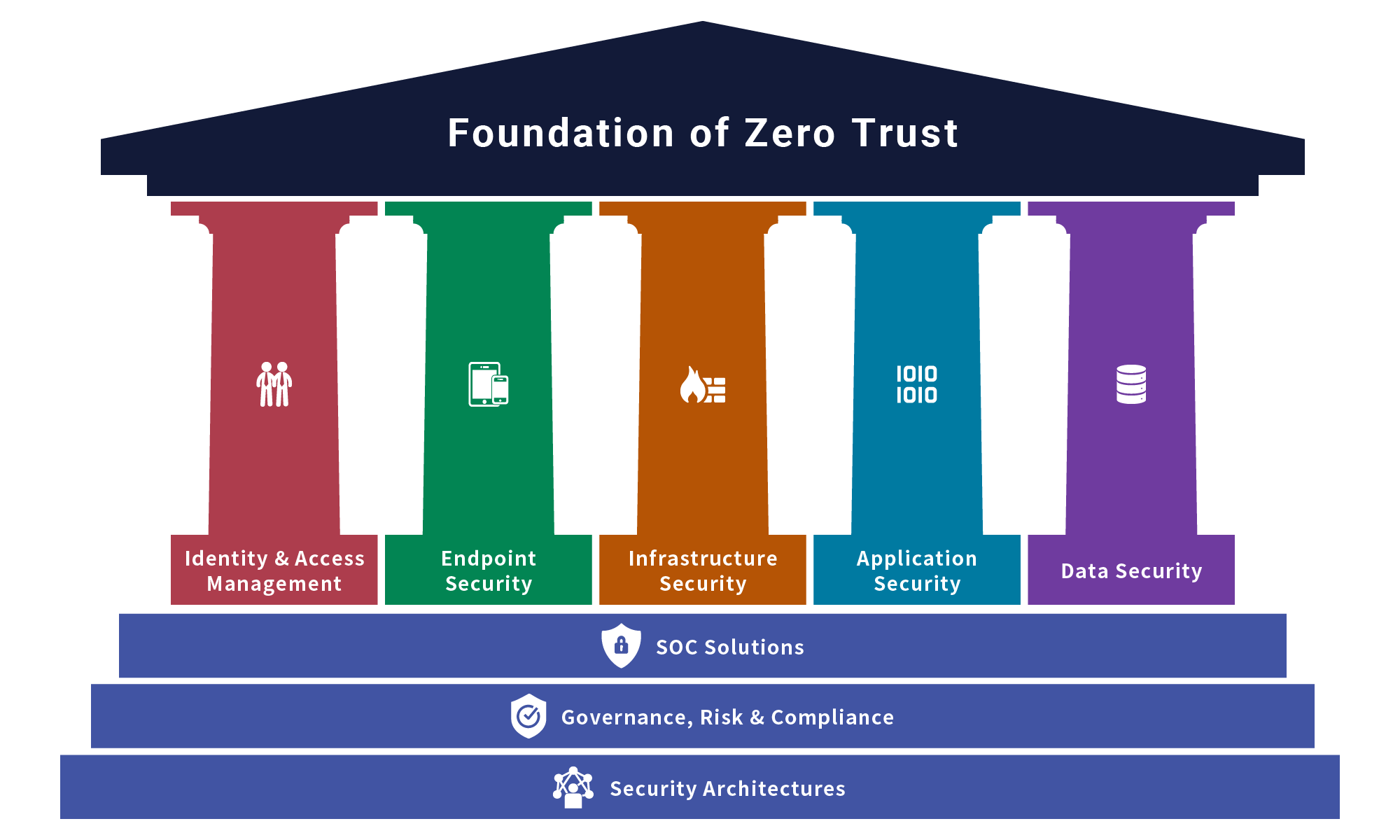
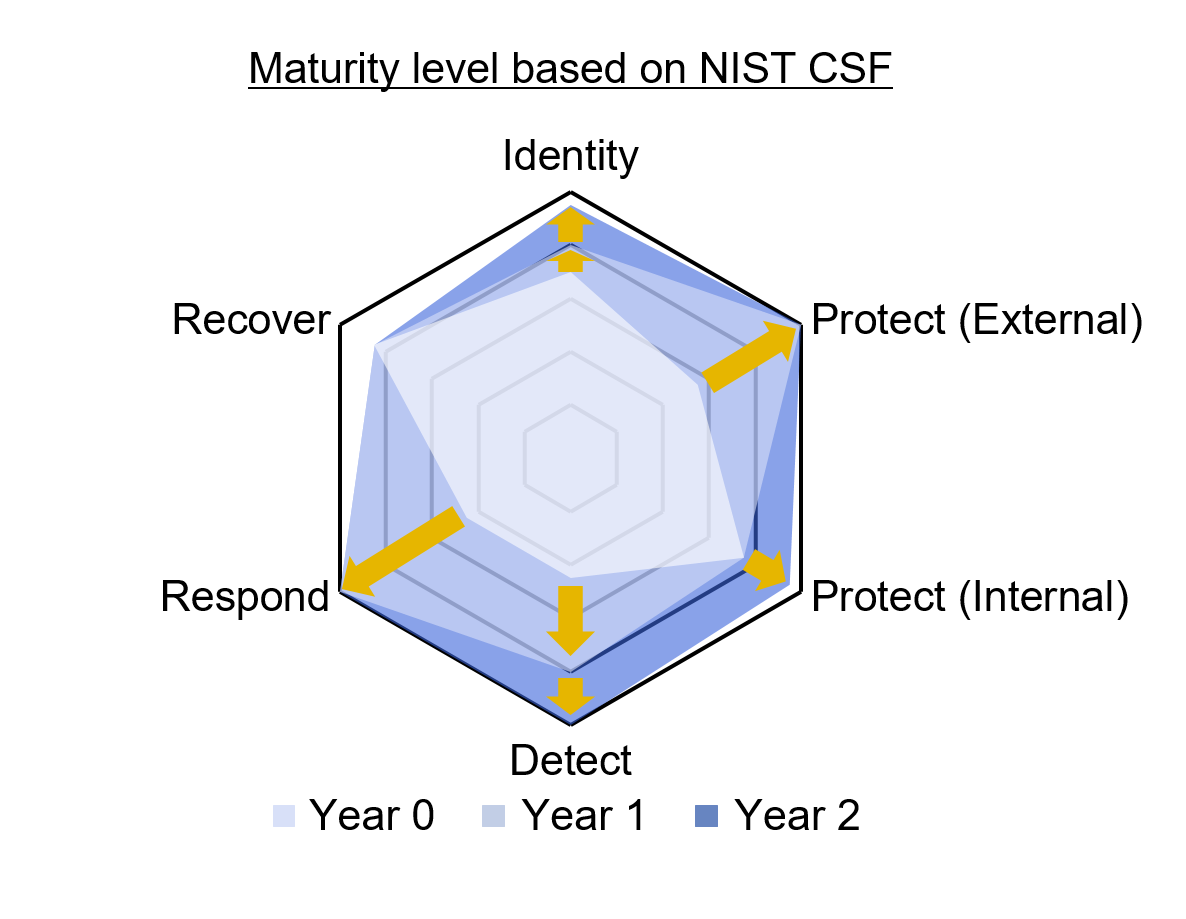
NTT DATA made a head start in the completion of a Zero Trust architecture. The leading principle of Zero Trust is “Never Trust, Always Verify”. Zero Trust is composed of various elements necessary for a reliable security framework. NTT DATA will provide a full range of end-to-end security services from consulting to implementation and managed services of Zero Trust combining multiple services of our portfolio and the know-hows that we have obtained through years of experience.

Identities represent people, services, or devices and the most important control point. We provide meticulous administration and precise control over user identities and access privileges to ensure secure and authorized access with an end-to-end approach.








Data flows to various endpoints once access is granted: corporate-managed, IoT, smartphones, BYOD, and partner-managed. We revolve around the specialized safeguarding and fortification of various endpoints with antimalware protection.








Network controls enhance visibility and prevent lateral movement for data access. We support the identification, protection, detection, response, and recovery of an organization’s network infrastructure from various cyber threats and potential risks.












Apps and APIs enable data consumption, varying from legacy on-premises to cloud-native ones. We offer specialized measures for assessing, enhancing, and safeguarding software applications, from web application firewalls.







Data should be safeguarded even when it leaves controlled devices, apps, infrastructure, and networks. We implement best practices, encryption, access controls, and monitoring to protect sensitive data information.





Organizations face the challenge of limited quality security resources and need efficient security solutions to enable faster threat identification and resolution. We offer a comprehensive suite of capabilities, including SIEM integration, SOAR optimization, and real-time continuous monitoring.




Security governance is essential for the Zero Trust architecture, serving as its foundation. Cutting-edge technology alone won't maintain it. We help effective global governance including establishing rules, ensuring compliance, and training people.

We can design and build a Zero Trust architecture tailored to the customer's environment with an alignment of cybersecurity, corporate, and IT strategies.
Success Stories and Latest Insights
Success Stories
Read how companies in various industries solved their challenges by partnering with NTT DATA.

NTT's Contribution to Olympic and Paralympic Games Tokyo 2020
NTT Corporation, as a Olympic and Paralympic Games Tokyo 2020 Gold Partner, provided telecommunications services, network security for telecommunication services and various cybersecurity measures and contributed to the stable operation.
READ THE NEWS

One-Stop Support of Global Governance Structure for a Global Manufacturer Group
NTT DATA helped a global manufacturer with 15 group companies with rougly 30,000 employees around the world and provided a one-stop support from consulting, and implementation to operation of Zero-trust security architecture.
READ THE STORY

Managing the Detection and Response Service for a Tobacco Giant
NTT DATA worked with a global tobacco giant to evolve their threat management capabilities and implemented a next generation SIEM with zenSIEM and zenSOC.
READ THE STORY

Incident Response and MDR Service for Operational Technology
NTT DATA helped a leading manufacturer of construction materials recover a ransomware attack by providing a local incident response service and implementing a threat detection solutions, such as Fortigate and FortiEDR.
READ THE STORY

Monitoring and Incident Response for a Railway Company
NTT DATA helped a leading railway provider after a severe security incident by providing services in monitoring and incident response, digital forensics and threat hunting and establishing a mid/long-term security improvement plan.
READ THE STORY

NTT DATA’s Security Journey: “ZEN Project”
NTT DATA Group has over 140,000 employees in 55 countries, and its group companies had different levels of security protection. The group modernized its security governance with a model based on Zero Trust, global governance, and SOC.
READ THE STORY
Latest Insights
Read our latest insights on Zero Trust-related topics from around the world.

Zero Trust: Your Digital Transformation Requires a Risk Transformation
A parallel cybersecurity strategy is required to modernize your technology landscape to combat a corporate firewall no longer protecting your data and users. While the cloud can provide unsurpassed agility, it can also expose new threat vectors. Your digital transformation must be accompanied by an innovative and comprehensive approach to reduce risk and attack surfaces.
DOWNLOAD (PDF: 839KB)

Cyber Without Perimeters: Getting Your Zero Trust Journey with Identity
We explore the identity-based zero-trust approach in detail and provide a maturity assessment framework to help enterprises understand their current position and how they can progress in their zero-trust journey. Additionally, the report highlights the benefits of zero trust, such as improved employee experience, reduced legacy technical debt, decreased third-party risks, and improved compliance.
DOWNLOAD (PDF: 1.6MB)
Zero Trust Services in Your Country
We provide our zero trust services in the following countries. Follow the link to find out what specific services are available in your country.
NTT DATA Services
NTT DATA EMEAL
NTT Ltd.
NTT DATA
For Other Services
Select a country below to explore other services and solutions available in your country.
Webinar
Register for future webinars or watch the past webinar archive videos to gain insights on zero trust and cybersecurity. To watch the past webinar archive videos, you will first need to register with BrightTALK.
More Stories from Our Blogs
Read our latest thinking, case studies, success stories, and more on our global blog, NTT DATA Focus, and on blogs in various countries.

8 Critical Areas for Your Next CIAM Implementation
READ THE ARTICLE

Evolving Security to Meet the Challenges of the Cloud, Part 2
READ THE ARTICLE

Evolving Security to Meet the Challenges of the Cloud, Part 1
READ THE ARTICLE

Best Practices for Identity and Access To Enable Zero Trust
READ THE ARTICLE

Implement Conditional Access to support Zero Trust Architecture
READ THE ARTICLE

NTT DATA’s identity journey towards Zero Trust
READ THE ARTICLE

NTT DATA’s Zero Trust Journey, Part Two: NTT DATA’s Zero Trust Architecture (and What We’ve Learned)
READ THE ARTICLE

NTT DATA’s Zero Trust Journey, Part One: Blazing the Trail
READ MORE