
Know the Selection Points of Zero Trust Solutions!
In today's age, systems are becoming more cloud-based, teleworking is becoming more widespread, and cyber-attacks are becoming increasingly sophisticated. It is difficult to sufficiently defend against threats with conventional perimeter defense security models, and "zero trust security" is increasingly being introduced as a solution. However, there are a wide range of solutions that implement zero trust security, making it challenging to evaluate and select the right one. In this article, we will explain the evaluation criteria and key points for selecting zero trust security solutions, with a particular focus on desk evaluation.
Those who are considering zero trust introduction but do not know what point to evaluate the solutions, or those who want to get an overview of zero trust security solutions first, should read this article.
1 What is Zero Trust Security?
Zero trust security is a model based on the premise of not trusting any internal or external networks and devices, assuming threats may be present. There is no distinction between internal and external; all access requests are always verified and only allowed if deemed trustworthy. This approach makes the entire network more secure.
2 Key Components of Zero Trust Security
Zero trust security requires a solution that covers the following key areas: (Table 1)
| Areas | Description |
|---|---|
| IDaaS (Identity as a Service) | IDaaS is a cloud-based authentication and authorization service that provides functions such as multi-factor authentication (*1) and single sign-on (*2). It centrally manages user and device identities and strengthens access control. |
| EDR (Endpoint Detection and Response) | EDR is a solution for detecting and responding to threats at endpoints (*3). It protects against known and unknown threats, and swiftly responds to and contains attacks when they occur. |
| UEM (Unified Endpoint Management) | UEM is a solution for centrally managing a wide variety of devices, including Windows, macOS, Android, and iOS. It automates device security settings and application distribution to improve management efficiency and security. |
| SASE (Secure Access Service Edge) | SASE is a cloud-based solution that integrates network and security functions. It provides functions such as SWG (*4), CASB (*5), and ZTNA (*6) to provide secure access to the Internet and cloud services. |
| SIEM (Security Information and Event Management) | SIEM is a solution for integrated management of security information and events. It performs log collection, correlation analysis, and abnormal behavior detection to streamline and automate incident response. |
Table 1: Major Components of Zero Trust Security
A method of authenticating a user with multiple elements, such as a fingerprint, facial recognition, or one-time password, in addition to a password. It reduces the risk of unauthorized access and enhances security.
A mechanism that enables users to access multiple apps and services with a single login. It enhances user convenience and simplifies password management.
A terminal device connected to a network. This includes PCs and smartphones and is important for security measures.
A security function that monitors and controls web traffic when using the Internet to prevent access to malware and unauthorized sites. It helps users in an organization to use the web safely.
A solution that monitors and controls access to cloud services to ensure security and compliance. It visualizes the usage of cloud apps, protects data, and enforces policies.
A network access method that authenticates and authorizes users and devices based on the zero-trust principle and grants them minimum access rights. It provides secure remote access instead of VPN.
3 Process of Solution Evaluation (Desktop)
When introducing zero-trust security, the optimal solution is selected through a process that includes requirement definition, market research, desktop evaluation, and actual machine evaluation. This section explains the evaluation points and methods used in the desktop evaluation.
3.1 Main Evaluation Points
When selecting a zero-trust security solution, a clear evaluation point is essential. We recommend that you organize the evaluation into functional and non-functional requirements.
- Functional requirements: These are requirements that indicate what the solution should achieve and evaluate whether it has sufficient required functionality.
- Non-functional requirements: These are requirements that indicate quality, limitations, and how the solution should be achieved, and evaluate reliability, scalability, and ease of use.
The following describes the main evaluation points for functional requirements (Perspectives by Solution Area, Table 2) and non-functional requirements (Common evaluation perspectives, Table 3).
| Areas | Main | Evaluation Points Description |
|---|---|---|
| IDaaS | Authentication and Access Management | Ability to provide secure and flexible access control by supporting a variety of authentication methods, including multi-factor authentication and single-sign-on risk-based authentication |
| User Lifecycle Management | Ability to automate the creation, modification, and deletion of user accounts to streamline directory service integration and provisioning | |
| Security Policy and Compliance | Ability to meet security and compliance requirements, including fine-grained access policy settings and integration with device authentication | |
| EDR | Advanced Threat Protection | Ability to protect endpoints from known and unknown threats through multi-layered defense capabilities, anti-ransomware, and vulnerability management |
| Real-time detection, response, and recovery | Ability to quickly identify and respond to threats through real-time investigation capabilities, automated response capabilities, and remote operation capabilities | |
| Endpoint Management and Control | Ability to provide comprehensive management and control of endpoints through application control, external device management, and detailed log collection | |
| UEM | Device Lifecycle Management | Ability to centrally manage a variety of devices through OS/patch management and asset management |
| Applications and data security | Ability to protect corporate data and applications through application distribution and management, data encryption, and remote wipe functions (*7) | |
| Policy application and compliance management | Ability to flexibly set and apply security policies, group management, and compliance monitoring to maintain organization-wide security standards | |
| SASE | Secure access control | Ability to provide secure access to users and devices anywhere through strict authentication, cloud application management, and remote access control |
| Integrated Threat Protection | Ability to comprehensively protect networks and endpoints through cloud-based firewall, antimalware, and DNS security | |
| Data protection and visualization | DLP (*8) • Encryption • Visualization of traffic and cloud application usage to protect sensitive data and ensure the transparency of the entire network | |
| SIEM | Data collection and analysis | Data collection from various log sources, normalization, real-time analysis, and correlation analysis to comprehensively understand security events |
| Threat detection | Advanced threat detection through preset alert rules, integration with the MITRE ATT & CK framework (*9), and user behavior analysis (UEBA) using machine learning | |
| Response automation | Function to automate workflows from incident detection to response according to playbooks created (SOAR) | |
| Visualization and reporting | Ability to visualize the security status and support decision-making through customizable dashboards, detailed reporting, and linkage with external threat information |
Table 2: Functional Requirements (Evaluation Points by Solution Area)
This function allows you to remotely wipe data in the event of device loss or theft. It helps prevent leakage of confidential information.
This technology and mechanism prevents unauthorized removal and leakage of confidential data. It enhances information security by monitoring and controlling data leakage.
This is a knowledge base that systematically summarizes cyber-attack techniques and tactics. It is used to understand attacks and formulate defense measures.
| Main Evaluation Points | Description |
|---|---|
| Availability | Check the operating time of the solution, frequency of downtime (SLA (*10)), redundancy mechanism, and impact of maintenance. |
| Performance | Check the response speed of the system and the capacity to handle the amount of throughput traffic. For example, EDR and SIEM require the ability to process large amounts of data in real time, while SASE requires management of network latency and bandwidth. |
| Scalability | Check the capacity of the system to handle the increasing number of users and data, license flexibility, and multi-device support. For example, IDaaS and UEM require the ease of adding new users and devices, while SIEM requires scalability to handle log data growth. |
| Migration and Integration | Check the ease of data migration from existing systems, whether it is cloud native, and the ability to integrate with other systems and services. For example, it is important to consider whether SaaS that can be linked is rich in other solutions, whether SIEM that can be linked with logs is rich, and whether IDaaS can be smoothly migrated from an existing authentication system. |
| Security | Check the strength of authentication and authorization, mechanisms such as data encryption, security certification and compliance. |
| Usability | Check the usability of the system, ease of viewing and customizing the dashboard, intuitive interface, and ease of setup and management. |
| Support | Check the vendor's support system (24 hours a day, 365 days a year, support language), documentation, and prompt troubleshooting. It is important that the support after installation is adequate and that problems can be promptly addressed. |
Table 3: Non-functional requirements (common evaluation perspective)
An agreement between a service provider and a user regarding service quality and availability. It includes indicators such as utilization rate, response time, and support system.
3.2 Evaluation Methods and Results
The main evaluation points described in Section 3.1 are just an outline. In an actual solution evaluation, it is important to expand these points into a detailed evaluation sheet. In addition to general criteria, you should clarify your company's specific issues and requirements, creating an evaluation sheet that addresses both general and in-house needs.
After creating the evaluation sheet, investigate each item through document reviews and interviews with vendors. Ultimately, conduct a comprehensive evaluation by organizing the scoring (e.g., "0: Not meeting requirements," "1: Meeting requirements," "2: Exceeding requirements with advantages over other solutions") and the satisfaction rate of the requirements. Also, include prerequisites for adopting the solution, such as service regions, supported languages, and costs, in the evaluation criteria (Figures 1 and 2)
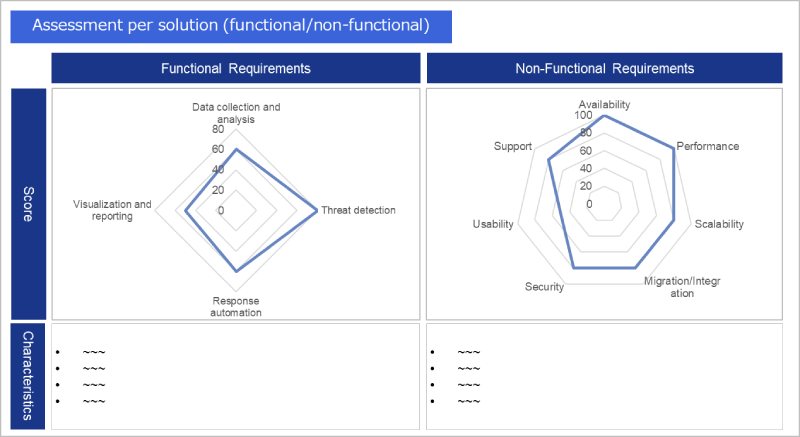
Figure 1: Example evaluation results of functional and non-functional requirements for each solution
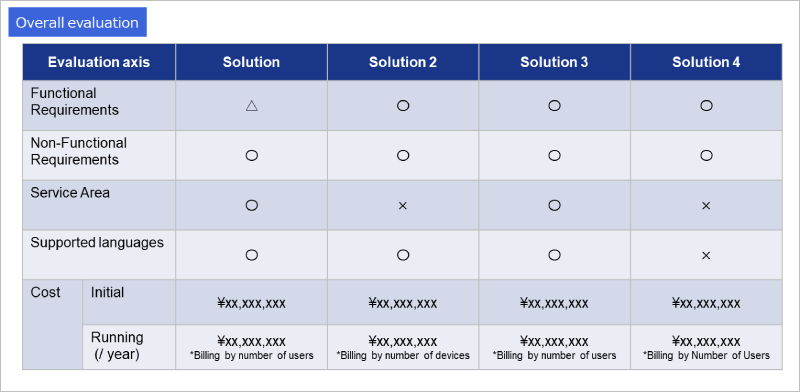
Figure 2: Example overall evaluation
4 Key Points in Selecting a Solution
When selecting a zero trust security solution, keep the following points in mind to ensure an effective and appropriate selection.
4.1 Clarifying the Purpose
To avoid introducing zero trust security as an objective, set specific goals such as strengthening your organization's security and improving operational efficiency. With a clear purpose, the process from selection to implementation and operation will be consistent, allowing you to achieve the maximum effect.
4.2 Importance of On-Machine Verification
On-machine verification, in addition to desk evaluation, enables you to confirm functionality, performance, and usability in an actual operating environment. The information obtained through on-machine verification, such as performance, compatibility, and operability, is crucial in selecting a solution. Use the desk evaluation to narrow down your options, and then conduct on-machine verification before making a final selection.
4.3 Checking the vendor's track record and reliability
In addition to the evaluation of the solution, the vendor's track record and market reputation are important criteria for selecting a vendor. Check the implementation record, positioning by a third-party evaluation organization, and support system to select a highly reliable vendor.
4.4 Choosing between best-of-breed and suite solutions
There are two types of solutions: best-of-breed, in which the most appropriate solution is introduced individually in each area, and suite, in which a single integrated solution is introduced. Each type has advantages and disadvantages, so choose one according to your company's situation and needs.
4.5 Including the perspective of operational issues in the evaluation
When you are operating an existing security solution, not only with zero Trust, but it is also effective to include the operational issues (Examples: lack of error logs, configuration export not possible, alert customization not possible, configuration limit too small, GUI not supported) in the evaluation of the new solution. Hear the operational issues of the operation unit and add elements that can improve operational efficiency to the evaluation.
5 Conclusion
Zero trust security is a crucial approach to achieving a flexible and secure IT environment. When selecting a solution, it is necessary to accurately understand the characteristics and requirements of each component and identify the best solution for the current problem. By pinpointing the appropriate selection criteria and effectively implementing zero trust security, you can dramatically enhance your enterprise's security level.

Ryota Sakaya
NTT DATA Japan Corporation
After joining NTT DATA, he has experience in financial system development and maintenance and security operations from 2012 to 2021, and security consulting and security inspection from 2022. He has strengths in both cyber security and project management.
Related links
