
Strengthen Security with SBOM in the Automotive Industry!
The automotive industry is advancing with the integration of various latest technologies such as AI and autonomous driving. While their convenience and comfortability tend to attract attention, we must also be aware of the increased cyber security risks due to the growing complexity and scale of the software used to realize these functions. In other words, it is required to prepare for security risks by clarifying the composition of software so that vulnerabilities can be addressed immediately and appropriately. In recent years, SBOM (Software Bill of Materials) has been attracting attention as a concrete method for this purpose. This paper describes the introduction of SBOM in the automotive industry and introduces the SBOM support services that NTT DATA can provide.
1. Changes in the Automotive Industry
The concept of the automotive has changed significantly with the introduction of connected functions and autonomous driving functions toward the realization of CASE*1. In order to realize new functions, AI-related companies are participating in software development one after another, and the complexity of the supply chain is inevitable. In addition, the number of ECUs (Electronic Control Units) installed in automobiles is projected to increase from an average of 29.6 per automobile in 2021 to 46.6 by 2035*2. As a result, the number of lines of software code is predicted to increase rapidly, reaching 200 million lines per automobile in 2020 and 600 million lines per automobile in 2025*3, surpassing that of software in other fields. (Figure 1, 2)
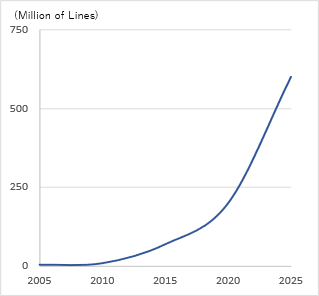
Figure 1: Changes in the number of lines of code in an automobile*3

Figure 2: Number of lines of program code in each field*4
In response to these changes, many automotive component manufacturers (suppliers) are trying to improve the efficiency of software development through the use of OSS. On the other hand, software becomes a complex and intricate structure, with some suppliers integrating OSS themselves and others adopting software with which OSS is already integrated. Therefore, without a full understanding of what software is embedded in which components, it is impossible to instantly assess the impact of OSS vulnerabilities on the developed system. Cyber-attacks against vehicles require adequate security measures since such attacks can lead to accidents involving human lives, such as remote control by attackers in the case of autonomous vehicles.
- *1 Acronym for Connected, Autonomous, Shared & Services, and Electric
-
*2
Total survey of On-vehicle electrical devices and components 2022 Volume 2
https://www.fcr.co.jp/pr/22053.htm -
*3
Cars are Made of Code
https://www.nxp.com/company/blog/cars-are-made-of-code:BL-CARS-MADE-CODE - *4 Ministry of Economy, Trade and Industry & Nissay Asset Management & Quora & FOSSBYTES & Windows Report
2. Can't sell cars?
Against this background, cyber security regulations and guidelines in the automotive industry have been developed. UN-R155*5 and UN-R156*6, both of which were issued by the United Nations, require measures for cyber security and software updates. It also mandates software composition and version control as well as vulnerability management throughout the supply chain and will not allow automobiles to be sold in the signatory countries if the measures cannot be validated.
ISO/SAE 21434, an international standard for automobile cyber security, states the need for vulnerability analysis and management throughout the entire lifecycle of a vehicle, from development to disposal. Because the lifespan of an automobile can be as long as 10~15 years, the period of responsibility for vulnerability management is significantly longer than that of a typical IT product.
-
*5
UN Regulation No. 155 - Cyber security and cyber security management system
https://unece.org/transport/documents/2021/03/standards/un-regulation-no-155-cyber-security-and-cyber-security -
*6
UN Regulation No. 156 - Software update and software update management system
https://unece.org/transport/documents/2021/03/standards/un-regulation-no-156-software-update-and-software-update
3. What is SBOM?
However, as mentioned earlier, with the increasing complexity of the supply chain and the number of lines of software code, it is not easy to understand all software components, including OSS, and manage vulnerabilities. So how do we manage them? The U.S. Executive Order*7 issued in 2021 and the EU CRA*8 which is under discussion as of December 2023, provide concrete measures to strengthen security in the increasingly complex software supply chain. The method is called the Software Bill of Materials (SBOM). SBOM is applicable to a wide variety of software, and it is also useful for automotive software, which has complex responsibilities and dependencies.
An SBOM is a list of software components and their related information in a machine-processable format.
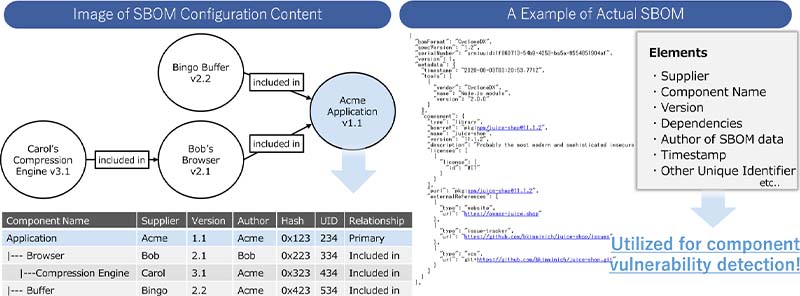
Figure 3: Conceptual image of SBOM and an example of actual SBOM*9
As shown in Figure 3, an SBOM consists of information such as supplier name, component name, component version, dependencies, SBOM author, timestamp, and other unique identifiers. This enables centralized vulnerability management for software with complex dependencies and structures created outside the company.
- *7 Executive Order on Improving the Nation's Cybersecurity
- *8 EU Cyber Resilience Act
-
*9
NTIA, Framing Software Component Transparency: Establishing a Common Software Bill of Materials (SBOM)
https://www.ntia.gov/files/ntia/publications/ntia_sbom_framing_2nd_edition_20211021.pdf
4. SBOM in the Automotive Industry
SBOM creation for vehicles covers a wide range of subjects, including embedded systems, real-time operating systems, and proprietary software components specific to each vehicle function. The ideal way for OEMs*10 to create SBOMs is for each supplier to create an SBOM and collaborate them. This is because in the automotive industry, there are few cases where OEMs and Tier 1*11 directly develop software components, and most of them are developed by Tier 2*12 and Tier 3*13. (Figure 4)

Figure 4: Supply Chain for On-Vehicle Software
However, in reality, most suppliers and OEMs do not have an SBOM generation mechanism and do not have sufficient software information linkage, or do not have an SBOM operation system in place, such as managing the SBOM in Excel.
NTT DATA provides a variety of SBOM services that take advantage of its technological capabilities based on its extensive knowledge of IT and cyber security, as well as its global capabilities with many locations around the world. NTT DATA is capable of developing a global system for providing managed services that comprehensively and continuously manage supply chain security, including services that extract OSS information from ECUs (electronic control units) and other vehicle-specific software components at each stage of the supply chain to efficiently create SBOMs. NTT DATA also provides services that integrate SBOMs created at each stage and enable management on a single platform, and services that utilize that platform to monitor and respond to vulnerabilities. [*] NTT DATA aims to prevent cyber-attacks on vehicles by enabling various suppliers and OEMs to visualize the use of OSS libraries and identify vulnerabilities.
- *10 This term is used in the automotive industry to refer to a finished car manufacturer.
- *11 Tier 1: Suppliers such as general component manufacturers that are contracted from OEMs as primary contractors.
- *12 Tier 2: Suppliers such as semiconductor component manufacturers that deal directly with Tier 1
- *13 Tier 3: Suppliers such as semiconductor IP vendors (companies that provide functional blocks that make up LSI) that deal directly with Tier 2
5. Summary
As the number of lines of software code increases due to the impact of changes in the automotive industry, such as connected vehicles, and the supply chain becoming more complex, it is important to understand each software component and its complex dependencies and manage them to respond appropriately to vulnerabilities. In particular, cyber-attacks on vehicles can directly affect people's lives, so ensuring safety is strongly required, and various regulations require vulnerability management throughout the supply chain. SBOM is an effective means of vulnerability management methodology, but establishing a methodology and aligning it with traditional development processes are necessary to build and operate SBOM efficiently and effectively.
NTT DATA provides SBOM services that can support vehicle-specific software components such as embedded software, as well as consulting for UN regulations, security testing services, and VSOC (Vehicle SOC) monitoring services. By utilizing these various security services, we contribute to the protection of vehicles and the safety of human lives.
Ikumi Urabe
After joining NTT DATA, he has engaged in global strategy and service planning in automotive security and OT/IIoT security.

